
Korims provides multi-cloud services, and at the same time specializes in network and infrastructure, so it has different architecture plans for different DDoS attacks, and has successfully assisted many customers to resist DDoS attacks.
Welcome to contact Korims, my business and technical specialists will assist you by understanding your company's infrastructure and providing corresponding cloud defense solutions.
Korims provides multi-cloud services, and is also specialized in network and infrastructure, so it has different architecture plans for different DDoS attacks, and has successfully assisted many customers to resist DDoS attacks.
Welcome to contact Korims, my business and technical specialists will assist you by understanding your company's infrastructure and providing corresponding cloud defense solutions.
The full name of DDoS is Distributed Denial of Service, and the Chinese name is distributed denial of service attack; it is a derivative attack method of DOS (Denial of Service).
Suspicious connection requests from a single IP or a certain IP network segment.
Endpoint device logs show a large number of strange requests.
Connection requests with the same connection characteristics, such as a single region, a single time.
CPU and RAM usage on the machine skyrockets.
The service is suddenly interrupted, or the service access speed drops suddenly.
All of the above situations may be caused by DDoS attacks. You must check the records on the device side. If you have installed monitoring software such as MRTG (Multi Router Traffic Grapher), or contact your ISP provider, obtain MRTG graphs to confirm traffic or CPU usage.
The types of DDoS attacks are too numerous to list, so only the most common attack methods are introduced.
Layer3 - including IP Spoofing, IPSec, ICMP Attack, ARP Spoofing
a.ICMP[1] Flooding Attack:
Definition: The most common is the DOS-Ping flood attack, which sends a large number of Ping requests through the BOT. If it is sent by multiple BOTs, it is a DDoS Ping attack.
Solution: At present, almost all public clouds provide the Load Balance service of Anycast IP, which can further process and disperse ICMP requests through a large number of global nodes of the cloud provider;
At the same time, the ICMP function of the server can also be disabled to achieve the effect of protection.
Layer4-TCP
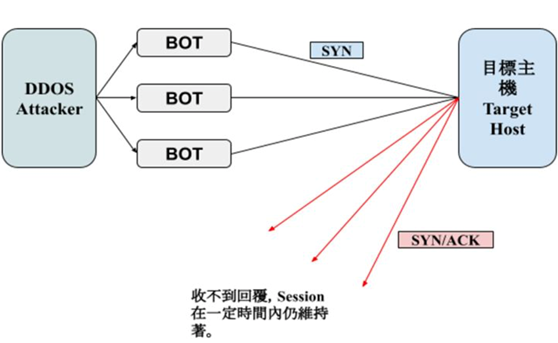
a. SYN flood attack
definition:
Attacks are carried out through the TCP handshake protocol [2], under normal circumstances:
Step 1: A server will send a SYN packet to establish the first connection.
Step 2: The B server that received the packet will return a SYN/ACK packet for confirmation.
Step 3: Server A returns an ACK packet to confirm the establishment of the connection.
After three steps, the connection can be established. However, a SYN flood attack uses multiple BOTs. After sending a SYN in the first step, the target server sends back a SYN/ACK packet, but does not return an ACK packet.
This is because the target server will open a temporary port to maintain the session after receiving the SYN packet, so the ports of the target server can be exhausted and the purpose of paralysis can be achieved.
Use cloud tools such as Anti-DDoS to import malicious traffic to the cleaning center for cleaning or black hole filtering.
Create a Proxy Server - usually a firewall, to replace the original server to establish an external connection. After confirming the establishment of the connection, the traffic will be imported into the original server.
Adjust the settings in the machine. When a new TCP connection flows in, it will overwrite the first temporary port that has not yet established a connection.
b. ACK flood attack
definition:
After three handshakes, a TCP connection is established, and the client will send an ACK packet at the end of the data transmission on the host side to confirm whether the data is normally transmitted, or whether the sequence is correct; the host side will consume computing resources when receiving the ACK packet. Check the status and content of the packet. If the packet shows that the data has not been transmitted normally, the data will be retransmitted.
Therefore, through the above mechanism, an attacker can use a large number of ACK packets to paralyze the host after the TCP connection is established, so that normal ACK packets cannot be responded.
Connect with the client through Anycast IP Proxy, and use cloud tools to judge whether the IP source is suspicious, and at the same time conduct attack detection. If attacked, the traffic will be automatically imported to the cleaning center for near-source cleaning.
Layer4 - UDPa.UDP Flood definition: UDP flood attack is a common UDP DDoS attack method. Since the UDP protocol is a non-connected protocol, the attacker sends a large number of UDP packets with any port number and forged IP to the host. When the host receives the UDP packet, it will consume resources to check whether there is a program receiving the packet at the port number; if there is no program receiving the packet at the port, it will send ICMP (Ping) to the sender. Through such a mechanism, attackers use a large number of zombie machines to send UDP packets, causing bandwidth load and exhaustion of the host side.


