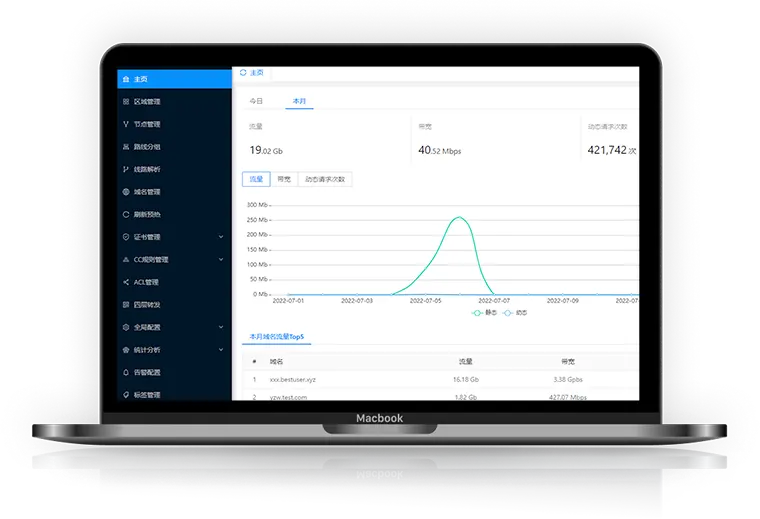
Alibaba Cloud, a subsidiary of Alibaba Group, is the world's leading cloud computing and artificial intelligence technology company. Provide cloud server, cloud database, cloud security, cloud storage, enterprise application and industry solution services. Free and fast filing, 7x24 hours after-sales support.